Apr 1
2013
KeePass NFC: Unlock your KeePassDroid database with NFC
 I’m pleased to announce KeePassNFC, a stand-alone application which lets you use a rewritable NFC tag to unlock your KeePassDroid database. This is a follow-up to KeePassDroid: NFC Support (this is a better implementation of that same idea) and Idea: an NFC authentication scheme.
I’m pleased to announce KeePassNFC, a stand-alone application which lets you use a rewritable NFC tag to unlock your KeePassDroid database. This is a follow-up to KeePassDroid: NFC Support (this is a better implementation of that same idea) and Idea: an NFC authentication scheme.
To use it:
- Install KeePassNFC: Play store
- Set up your NFC tag
- Unlock your password database to your heart’s desire
To set up the tag, launch KeePassNFC:
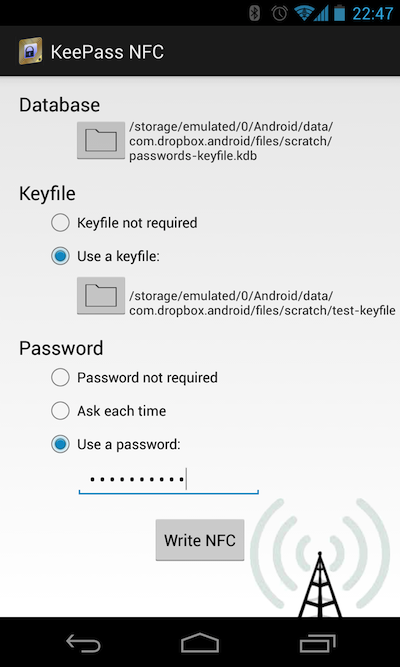
Here you must select a database, and then, optionally, a keyfile and password. The options are hopefully self-explanatory. Press “Write NFC” and hold an NFC tag near your device to program it, and you’re done.
Now, holding the tag near your device will automatically load KeePassNFC, which will decrypt your password using the data stored on the fob and launch KeePassDroid.
KeePassNFC is open source, and you may download the source code.
Questions:
- Why two separate apps? KeePassDroid has very few application permissions, which is good security practise. Using two separate apps means not having to give NFC permission to KeePassDroid itself.
- How secure is it? Reasonably. The NFC tag stores only random numbers, and the password itself is encrypted with those numbers. So an attacker would have to scan your NFC tag and either steal or root your Android device to get your password. If you suspect that your NFC tag has been read, you can use KeePassNFC to re-write it with new random values, rendering the previous information useless.
Update: A previous version of this blog included a custom version of KeePassDroid. I’m pleased to say that the current version of KeePassDroid in the Play store incorporates the required changes (technical: it supports being supplied a database password via an Intent), so my custom version isn’t required. For the curious: here is the source code for the required changes.
This NFC implementation grew out of discussion on the KeePassDroid forums. You can view and add to that conversation at Google Groups’ KeePassDroid forum.
